I took this how to from a document I wrote some time back but the information herein is still accurate for how to recover a domain controller. At the time i was working at an insurance firm and managed 6 domains. Budget was low and found that the domain controllers was on regular PCs. Needless to say they weren't reliable. I found myself using this procedure regulary for domain controller recover.
I hope this has been informative for you. Like,share and comment.
Preparing a New Server
a. Reinstall the Operating System using Windows Server 2008 R2/2012 R2
b. Give it a temporary name and IP, just to connect to the network and get updates etc.
c. Install all current updates and service packs
d. Install Antivirus
e. Install DNS
f. Install and configure SNMP
g. Then wait until AD is ready
Preparing Active Directory
a. Seizing Roles
i. On another domain controller in the same domain as the failing DC determine what roles the failing server had by typing
netdom query FSMO at the command prompt

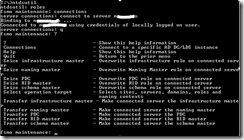
ii. Seize the roles on a command prompt by typing in the following (See Figure Below)
iii.
Ntdsutil ENTER
iv.
Roles ENTER
v.
Connections ENTER
vi.
connect to server <servername>, where servername is the name of the server you want to use, and then press ENTER
vii.
q ENTER
viii.
? “For a list of roles you can seize”
ix.
Seize Role <role you want to seize>
b. Cleaning up MetaData in Active Directory
This is the process of removing the failed Domain Controller from Active Directory.
WARNING!! Please take note that using the
ntdsutil utility incorrectly can have serious negative consequences on Active Directory. If you not sure DONT DO IT! J
i. At the command line, type
Ntdsutil and press ENTER.
ii. At the Ntdsutil: prompt, type
metadata cleanup and press Enter
iii. At the metadata cleanup: prompt, type
connections and press Enter
iv. At the server connections: prompt, type
connect to server <servername>, where <servername> is the domain controller (any functional domain controller in the same domain) from which you plan to clean up the metadata of the failed domain controller. Press Enter.
v. Type
quit and press Enter to return you to the metadata cleanup: prompt.
vi. Type
select operation target and press Enter.
vii. Type
list domains and press Enter. This lists all domains in the forest with a number associated with each.
viii. Type
select domain <number>, where <number> is the number corresponding to the domain in which the failed server was located. Press Enter.
ix. Type
list sites and press Enter.
x. Type
select site <number>, where <number> refers to the number of the site in which the domain controller was a member. Press Enter.
xi. Type
list servers in site and press Enter. This will list all servers in that site with a corresponding number.
xii. Type
select server <number> and press Enter, where <number> refers to the domain controller to be removed.
xiii. Type
quit and press Enter. The Metadata cleanup menu is displayed.
xiv. Type
remove selected server and press Enter.
You will received a warning message. Read it, and if you agree , press Yes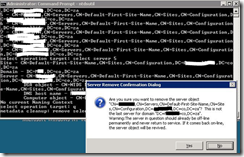
xv.
At this point, Active Directory confirms that the domain controller was removed successfully. If you receive an error that the object could not be found, Active Directory might have already removed from the domain controller.

xvi. Type
quit, and press Enter until you return to the command prompt.
xvii. Metadata clean is now complete and you can continue with the next step of setting up the server to connect to AD again.
Setting up the replacement server
Switch on the new server, at this stage it is already setup.
i. Make sure the new machine has the correct hostname and IP address. The hostname will be identical to the failed machine.
ii. Go start run and type in DCPROMO
iii. Follow the steps of adding a NEW domain controller in an EXISTING domain. Join it to the same domain the failing DC was in.
iv. Make sure DNS is selected.
v. The installation will begin
vi. After it has replicated you will get a screen to say its complete.
vii. DNS will automatically populate because Active directory Integrated zones are being used.
viii. Reboot the server, check if everything is working
ix. Recovery is COMPLETE!!
Important Notes:
a. The five FSMO roles are:
· Schema master - Forest-wide and one per forest.
· Domain naming master - Forest-wide and one per forest.
· RID master - Domain-specific and one for each domain.
· PDC - PDC Emulator is domain-specific and one for each domain.
· Infrastructure master - Domain-specific and one for each domain.
b. What will happen if you don’t perform the seize in time?
| FSMO Role | Loss implications |
| Schema | The schema cannot be extended. However, in the short term no one will notice a missing Schema Master unless you plan a schema upgrade during that time. |
| Domain Naming | Unless you are going to run DCPROMO, then you will not miss this FSMO role. |
| RID | Chances are good that the existing DCs will have enough unused RIDs to last some time, unless you're building hundreds of users or computer object per week. |
| PDC Emulator | Will be missed soon. NT 4.0 BDCs will not be able to replicate, there will be no time synchronization in the domain, you will probably not be able to change or troubleshoot group policies and password changes will become a problem. |
| Infrastructure | Group memberships may be incomplete. If you only have one domain, then there will be no impact. |
c. DO NOT seize this role on a Global Catalog!
Do not put the Infrastructure Master (IM) role on the same domain controller as the Global Catalog server. If the Infrastructure Master runs on a GC server it will stop updating object information because it does not contain any references to objects that it does not hold. This is because a GC server holds a partial replica of every object in the forest.
UNLESS all DCs are GC Servers
 their software and can never buy it outright and also means that whenever you want to study and prepare for an exam,you will have to fork out quite a hefty sum of money.
their software and can never buy it outright and also means that whenever you want to study and prepare for an exam,you will have to fork out quite a hefty sum of money.






















 Popular
Popular
 Tags
Tags
 Videos
Videos


